In my previous post on setting up a guest network, I explained how to setup a guest network using a separate VLAN. While this will mostly separate the guest network from the local network, there are several ports open to your Sophos XG device based on the guest network being assigned to the LAN zone. By default, the LAN zone has several ‘Local Service ACL’ settings enabled which you can view on the ‘Administration’ page under the ‘Device Access’ tab. As you can see in the picture below (ignore ‘Guest_LAN’ for now), various services such as HTTPS (TCP port 4444), SSH (TCP port 22) and DNS (TCP port 53) are enabled for the LAN zone.

While these services may be desired for your local network, you might not want any users or devices on your guest network to have access to these services/ports. To achieve this, we’ll create a separate zone for the guest network.
1. Access the ‘Zones’ tab on the ‘Network’ page and click ‘Add’ to create a new zone.
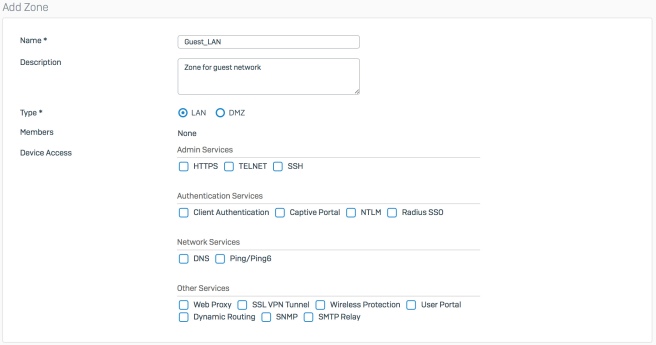
2. Provide a name for the zone such as “Guest_LAN” and a description. Select ‘LAN’ for the type and enable device access services as desired (i.e. services you want users in the Guest_LAN zone to be able to access on your Sophos XG device). For this example, we’ll keep everything unchecked since we want to completely isolate this zone. Click ‘Save’ at the bottom.
3. Access the ‘Interfaces’ tab and open the interface your guest network is on. On the ‘Edit VLAN’ page, update the ‘Zone’ setting and choose your newly created ‘Guest_LAN’ and click ‘Save’.

4. Access the ‘DHCP’ tab and open the guest DHCP server. If you had the guest DHCP server assigning the interface IP address as the DNS server (i.e. using Sophos XG’s DNS server), you’ll need to specify a different DNS server or select ‘Use Device’s DNS Settings’ to use whatever DNS servers you have set on the ‘DNS’ tab.

Note: If you would like to use the Sophos XG DNS server for the guest network, you can leave the interface IP address but DNS must be enabled for the ‘Guest_LAN’ zone. To change this, access the ‘Administration’ page and choose the ‘Device Access’ tab. On the ‘Guest_LAN’ row, select ‘DNS’ and click ‘Apply’. As a reminder, users on the guest network will have access to the DNS (TCP port 53) on your Sophos XG device.
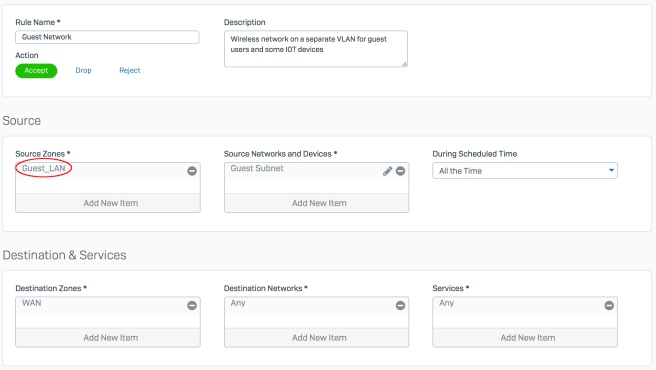
5. The last step is to add the ‘Guest_LAN’ zone and remove the ‘LAN’ zone (as required) from the ‘Source Zone’ on any firewall rules you for the guest network.
6. All done! Now your guest network is completely isolated from the local network. You can test this using a port scanning tool such as nmap from a device connected to the guest network.
Hi, great article! How can I allow guest users access to the local web servers without use my local windows dns server. When I change to 8.8.8.8 they can surfing on internet, but they can not access to my local web site. Then, if I modify the nat rule and add the guest LAN to the origin source, where is configured zone WAN, they can access to my local site. But technical support tell me that was a bad practice to do the last one
LikeLike
Hm, I would think you just need to create a normal firewall rule that allows the guest network/zone (source) to access the network/zone (destination) that the web server is on. If it’s just web access, then you could probably just specify the HTTP and HTTPS services. You might want to post this question on the official Sophos forums or Sophos reddit. I usually have pretty good luck finding a solution that way, but I’d imagine the above should work.
LikeLike